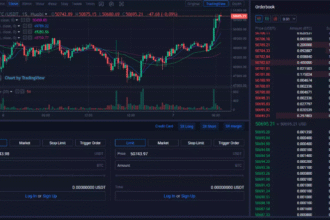
How To Create Crypto Staking Alerts | Step-by-Step Guide
In this article, I will explain the process of creating alerts for staking, which is a resourceful tool for managing…
Is Bridging Tokens Safe? A Comprehensive Guide to Risks and Security
In this article, I will address the question Are bridging tokens safe? With the increase in cross-chain activities, token bridges…
What If We Turned On Voyager’s Camera Today?
In this article, I will discuss the intriguing concept of reactivating Voyager's camera today. Voyager 1 and 2 have journeyed…
How To Create A Bridging Layer For Private Transactions
This article is to explain How To Create A Bridging Layer For Private Transactions. A bridging layer enables various blockchains…
How To Secure Bridging Liquidity From Hackers | Protect Your Assets
I am going to explain in this article how bridging liquidity can be secured from hackers. Protecting assets while moving…
Which Blockchains Have Built-in Privacy Features
In this article, I will analyze Which Blockchains Have Built-in Privacy Features. With the growing need for privacy in the…
10 Ways To Monitor Bridging Transaction Finality
In this article, I will discuss the Ways To Monitor Bridging Transaction Finality since they facilitate investment in a diversified…
Difference Between Bridging and Exchanging on a DEX
In the following article we will focus on the dissimilarity of bridging against exchanging on a DEX. Although both of…
How To Secure Bridging Oracles from Hacks
I will explain how bridging oracles can be protected from hacks in this article. This is a crucial aspect of…
What is Apple Business Manager? Know All Details
In this article, I' will talk about What is Apple Business Manager, including how it benefits organizations in controlling their…