I will explain how bridging oracles can be protected from hacks in this article. This is a crucial aspect of blockchain interoperability. With popularity, comes danger.
Oracles are exposed to various attacks, along with bridges. Furthermore, safe communication across multiple chains may result in avoiding critical losses due to exploitation, manipulation, or vulnerabilities within the contracts.
What is Bridging Oracles
Bridging oracles are distinct systems that enabling secure transfer of data and assets across different blockchain networks. They serve as middlemen, checking and passing on information such as token balance, transactions and smart contract interactions over several chains.
This support otherwise independent blockchains to communicate with each other. Bridging oracles are different from traditional oracles because they do not link blockchains to external data resources; rather, they emphasize communication between chains.
Their reliability is of utmost importance because any exposed weakness might cause significant exploitation, financial loss, or create systemic threats. Security can be maintained through decentralization, auditing, and strong consensus mechanisms that control the potential arrangements or attacks from being launched during data transfer.
How To Secure Bridging Oracles from Hacks
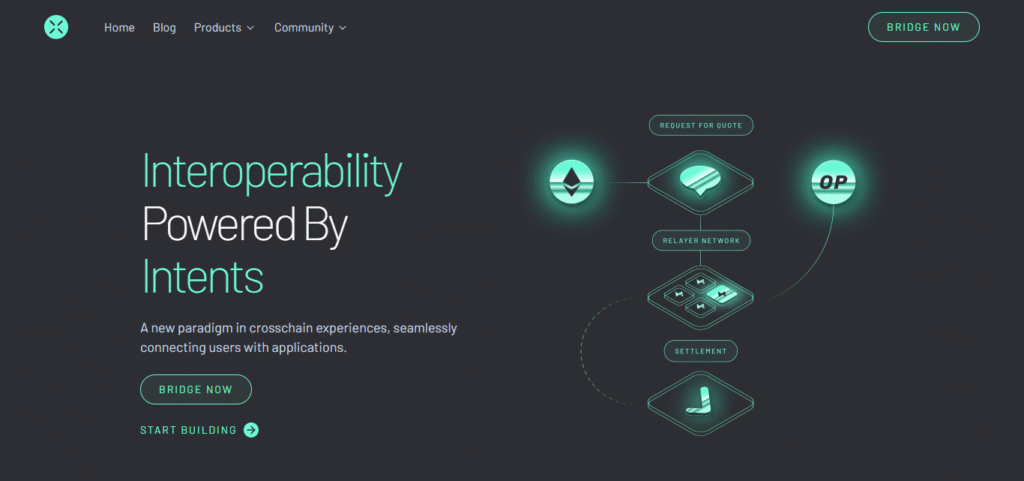
Across Protocol implements proprietary security methods to safeguard its bridging activities:
Canonical Assets
Unlike other bridges that utilize wrapped tokens, Across only uses canonical assets. This avoids the wrapped token vulnerabilities of infinite minting and redemption failure.
Intents-Based Architecture
Across transfers the risk from users to relayers. Relayers compete to pre-fund transfers, which guarantees the system’s safety during turbulent conditions.
Optimistic Oracle
The system uses UMA’s optimistic oracle which only requires one honest user for security. This statement reduces the chances of having centralized failure points.
Security Best Practices
Spread Out Some Risks By Sharding Oracle Nodes
These can include proof-of-work systems, alloced oracle, Permit Manager and many more. Using a federation of independent nodes can minimize the possibility of collusion as single point of failure. Orthogonality widens resistance and trust.
Add Multi Signature And Threshold Schemes Of Implementation
Guardians or validators need to be provided with messages so that they listen to instructions sent cross-chain. Threshold cryptography allows ⅔ be defined as manipulators.
Smart Contracts Audits Should Be Done Routinely
Conducting an audit of all contracts related to bridges and oracles, an association of security auditors should be obtained in advanced. Regular audits evolve over time and mitigate threats that are profound during certain periods of time.
Establish Intel SGX and Other TEEs
Using trusted execution environment when processing data off-chain serves as another approach to secure data. Additional form of resistance can also protect sensitive operations placed outside a chain.
Real Time Monitoring with Alerts
Implementing some level of monitoring tools can help spot any suspicious activity, such as verification attempts with abnormally high volumes. Automated alerts make responding to these threats speedy and efficient.
Add Circuit Breakers & Rate Limiting
Add smart contract logic to introduce the ability to stop bridge activity or throttle the number of transactions allowed if certain thresholds are met. This would make it possible to prevent fund draining by attackers in a single transaction.
Implement Cross Validation Between Chains
Use multiple blockchains or oracle providers to validate singular data and flag any discrepancies. Redundant validation can prevent single-source manipulation, and serve as a means of preventing cross verification inconsistencies.
Add Replay Attack Prevention Treatures
Manipulative attempts of resending authentic old messages (replay attacks) later on can be minimized by using nonces or unique identifiers in oracle messages.
Conduct Bug Bounty Programs
Reward has already been programmed can catch attention of white-hat hackers. Exposed systems attract malicious intentions, hence pre-emptive systems like Immunefi can prompt skilled testers to assess the system.
Monitor All Known Threat Intelligence Actively
Security concern that are related to monitor industry changes and contemporary espionage be actively advanced, as one needs to adapt with the pace of the threat landscape.
Why are bridging oracles vulnerable to hacks?
Bridging oracles have become attractive assets to capture because they facilitate the movement of assets and information between blockchains. Bridging oracles tend to have a lot of cross-chain liquidity, which makes them a target for hackers.
An attacker can shut down the entire bridge, thus making it useless on different blockchains, leading to unrecoverable costs and chaos across the linked blockchain systems.
However, hackers do not attack at random; they do have some points of entry. Some of the points include autonomous centralised blockchain validator sets, weak signature checking systems, and bug-ridden smart contracts and contracts that have not undergone auditing.
Pros and Cons of Securing Bridging Oracles from Hacks
| Security Measure | Pros | Cons |
|---|---|---|
| Decentralized Validator Networks | Reduces single points of failure; enhances trust | Can be slower and more complex to coordinate |
| Threshold/Multi-Signature Schemes | Prevents single-party control; adds strong consensus checks | Increased latency; added complexity in setup |
| Smart Contract Audits | Identifies and fixes vulnerabilities early | Expensive and not always 100% foolproof |
| Trusted Execution Environments (TEEs) | Enhances security for off-chain processes | Hardware-dependent; limited transparency |
| Real-Time Monitoring & Alerts | Allows quick detection and response to threats | Requires constant maintenance and tuning |
| Circuit Breakers & Rate Limiting | Minimizes damage in case of attack | May temporarily halt legitimate transactions |
| Bug Bounty Programs | Crowdsources security testing; cost-effective | Relies on external interest and honest disclosure |
| Cross-Validation Across Chains | Improves data integrity; detects discrepancies early | Adds complexity and possible overhead |
Conclusion
Finally, the securing of bridging oracles is critical to ensure the security and privacy of cross-chain ecosystems.
Implementing strong validation, continuous auditing, active monitoring, and decentralization in how projects are structured reduces the likelihood of hacks.
When securing assets, enabling interoperability, and creating long-term resilience within decentralized networks, a blockchain technology should always utilize a security-focused approach as it develops.